
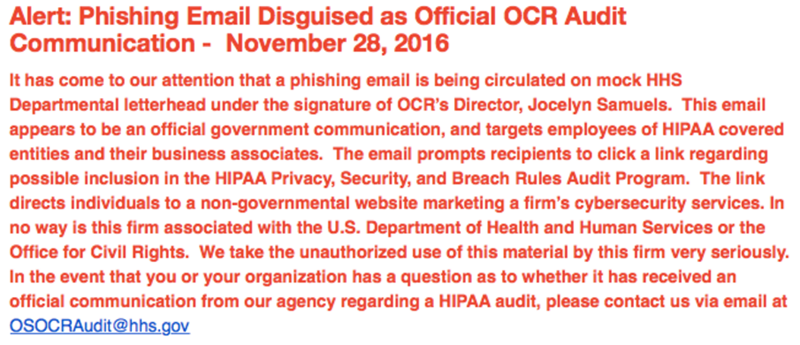
Healthcare executives have many things about which to worry, including cybercrime and an Office for Civil Rights (OCR) HIPAA Phase 2 audit. Now, in a move to double your pleasure/double your fun (with apologies to Wrigley’s Doublemint gum), cybercriminals are sending out fake OCR Phase 2 audit phishing emails. Here’s what the OCR has to say:

Take a close look at the two email addresses. Can you find the differences? The top one, at first glance, might appear to be a valid OCR email address. Note the concatenation of “hhs” and “gov” with a hyphen (“-”) and the use of the “.us” domain suffix. Even recipients who know that the correct domain is “hhs.gov” might be fooled unless they paid very close attention.
It was inevitable that a cybercriminal would take advantage of the OCR audit process and its reliance on email for notifying providers that they’re being audited. Since the announcement of the OCR HIPAA audit program, organizations should have put into place procedures for immediate escalation to the appropriate individuals of any audit notice received.
The process for appropriately handling an OCR audit notice now should be updated to include carefully checking email addresses (which may be hidden under an alias) and weblinks (which may be obscured by a misleading tag) in purported audit notice emails.
It also serves as a great example of how all employees need to be trained to use skepticism and common sense when opening and acting on emails.
More information on the OCR HIPAA audit program may be found at OCR HIPAA Audit.
Let’s be careful out there!

